Intro
Hello! Welcome to the introduction of my lab environment! Each and every aspect was enabled and created after months of working on live samples. First off I’ll explain my Malware analysis lab. It is quite straight forward but has minute details.
All the diagram and screenshots are my own
Malware Analysis Lab
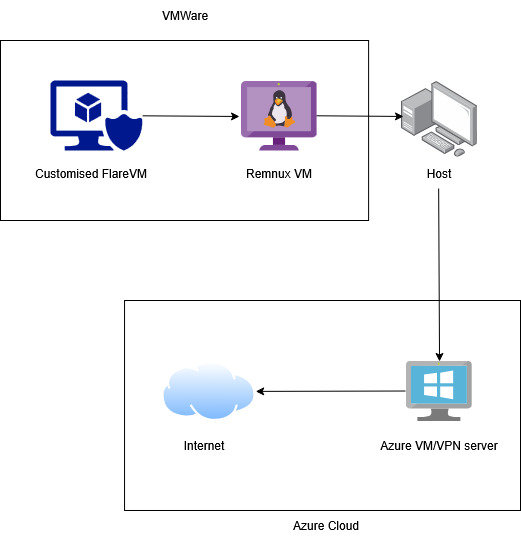
To begin with, I am using FlareVM by Mandiant. I did a minimal install due to storage concerns and installed tools as per my requirements. I also tried and removed VMware traces from this VM just for extra hardening and to make it more realistic. I have created dummy files, and made it so that it actually feels like a normal desktop. It is completely isolated from the host and it uses Remnx VM as a bastion host/firewall to access host/internet. So that I’d have complete control and monitoring over the network traffic to and from FlareVM.
RemnuxVM, I am mainly using for it’s intended purposes only, which is, for Linux binary RE. On top of that it acts as a bastion host, firewall, and a killswitch (custom script deployed to enable/disable internet for FlareVM). I also use it for inetsim and wireshark, as I prefer to keep the network tools off of FlareVM especially when doing dynamic analysis.
My host, is my trusty Ubuntu laptop. It hosts VMware and OpenVPN client. That’s pretty much all there is to it :)
The VPN server is the smallest possible Azure VM in a region somewhere in Asia(mostly). I have an ARM template to set up OpenVPN in my specified region. I like the VPN to be multi-region just as an added layer of security. Moreover it never takes more than 30 mins to do so. So for every new sample I tend to switch regions (Especially if it was a region specific attack). Though you might think that it is an overkill to have a new server for every sample, but it also allows me to freely scan and enumerate any IP or Host, especially with the help of SpiderFoot. So when you add that extra step, it starts to make sense. I host my own VPN server just cause it is free :)
And the last state is the Internet, the world where it all happens!
AD/IR Lab
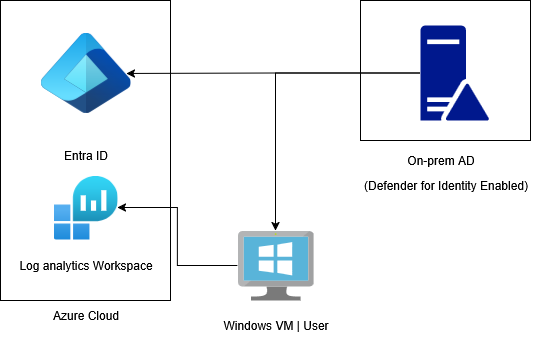
My second lab environment is a hybrid AD environment, consisting of a Microsoft Developer Subscription which includes entra ID, Defender for Identity and many more things for free :D. To make it an authentic environment, I am hosting another Domain Controller in Azure making it similar to real world environments. I have groups and roles on both Entra and “on-prem”. So a lot of identity action after initial compromise on my Windows VM.
To maintain and collect all the logs(Security Event IDs and Sysmon logs), I have a log analytics workspace, it collects logs from On-prem DC and the user device. And it seems that this is it for the environment.
It really doesn’t sound much but I guess when it comes to AD and Azure, setting it up properly takes time. I still do remember, AMA and DCR troubleshooting to get the desried logs and then trying to parse them in a decent format because I don’t have Security Events table as I am not using Sentinel (PS - Sentinel is expensive D:). And not to mention the roles and policies. If I start to explain those, It would take quite a long time and the article would go on for a while. All of the AD environment is inspired from the environments which I have seen in my Clients (There are like 20 clients. I have good security experience, PS - I am searching for a new job :D).
I intend to integrate my malware learnings and my forensic skills in this AD environment to boost my skill development.
You would be seeing a lot more of these environments in the coming environments! If you’d like to see the environments in detail, feel free to reach out!
